Accelerating Offensive R&D with Large Language Models
Mirrored from Outflank.
Introduction
At Outflank, we continually seek ways to accelerate our research and development efforts without compromising quality. In this pursuit, we’ve begun integrating large language models (LLMs) into our internal research workflows. While we’re still exploring the full potential of AI-powered offensive tooling, this post highlights how we’ve already used AI to speed up the delivery of traditional offensive capabilities.
This post details our exploration of the “trapped COM object” bug class, as identified by James Forshaw. Subsequently, IBM X-Force Red weaponized the technique for lateral movement, which further piqued our interest. Their lateral movement POC has five high-level steps:
- Set the registry keys required for reflective .NET execution (
AllowDCOMReflectionandOnlyUseLatestCLR) - Hijack the COM registration for
StdFontso it points to theSystem.Objectclass - Create an instance of the
WaaSRemediationAgentclass over DCOM - Access the type library reference for
stdoleand resolve theStdFontclass to create a “trapped” instance ofSystem.Object - Use .NET reflection on the
System.Objectinstance to invokeAssembly.Load
Both blog posts utilize the WaaSRemediationAgent COM class, which runs in a service with Protected Process Light (PPL). This attribute ultimately prevents the .NET runtime from loading into the WaaSMedicSvc service on Windows 11, rendering the approach ineffective on updated endpoints. This limitation is specific to the chosen COM class, however, rather than inherent to the bug class itself. Therefore, we attempted to identify an alternative COM class that met the requirements for lateral movement without relying on a PPL host process. In the remainder of this post, we’ll detail our journey to discover such alternatives.
Discovering Trapped COM Objects
We utilize a private framework inspired by collaborative architectures like Argusee for this type of research. We divided our process into two phases for the sake of explanation, but in practice, a single harness handles the entire workflow.
Enumeration
There are essentially two requirements for a lateral movement candidate in this bug class:
- DCOM-enabled
- Exposes a method capable of command/code execution
We built a simple C# program to hunt for these candidates by enumerating COM classes and dumping the results to JSON. Our collector discovers registered COM classes in the Windows registry and records various metadata, including method signatures, privilege levels, and referenced type libraries. While it’s straightforward to check if a class supports DCOM, determining whether it can actually execute code is more challenging. The resulting JSON gives us enough information to spot promising targets, but it cannot guarantee lateral movement opportunities. For this example, we simply filter for the referenced type library used by Forshaw to execute a .NET assembly.
Of course, there are other hijackable classes, as well as different code execution methods, that we can discover with a combination of filters. Since we aren’t training a model for this project, the gap between “mostly automated” and “fully automated” is huge. As such, the harness provides each POC to our team for manual review, followed by further automated testing. We found this collaborative approach to be significantly more straightforward.
Validation
We used GPT-4.1 to generate lateral movement POCs with the following prompts:
System
You are an expert Windows security researcher.
Your task is to analyze the provided example COM client code and generate similar working code for a different COM class with the same pattern.
Important guidelines:
1. Generate COMPLETE, WORKING C/C++ code - not templates or pseudocode
2. Include all necessary headers, imports, and dependencies
3. Use the exact CLSIDs, interface IDs, and type library GUIDs provided
4. Follow the same technique as the example
5. Add clear comments explaining each stepUser
Generate working COM client code in C/C++ based on this information:
## Primitive Information
```
{
"type": "trapped_object",
"vector": "IDispatch → ITypeInfo → StdOle → StdFont → System.Object → Assembly.Load",
"generation_hints": {
"pattern": "IDispatch → ITypeInfo → Type Library → CreateInstance → Trapped Object",
"critical_steps": [
"Instantiate the target COM object remotely",
"Get IDispatch interface and call GetTypeInfo",
"Navigate to containing type library",
"Find hijackable class (e.g., StdFont)",
"Use ITypeInfo.CreateInstance to get trapped object",
"Access .NET reflection through trapped object"
],
"registry_requirements": [
"AllowDCOMReflection=1",
"OnlyUseLatestCLR=1",
"TreatAs registry key for hijacking"
]
}
}
```
## COM Class Details
```
{
"clsid": "{2C941FC5-975B-59BE-A960-9A2A262853A5}",
"prog_id": "IMAPI2FS.MsftFileSystemImage.1",
"server_path": "C:\\Windows\\System32\\imapi2fs.dll",
"is_dcom_enabled": true,
"interfaces": [
{
"iid": "2c941fe1-975b-59be-a960-9a2a262853a5",
"name": "IFileSystemImage",
"has_idispatch": true
},
...Other attributes and interfaces left out for brevity
],
"referenced_type_libraries": [
{
"Name": "stdole",
"GUID": "00020430-0000-0000-c000-000000000046",
"Classes": [
{
"Name": "StdFont",
"CLSID": "0be35203-8f91-11ce-9de3-00aa004bb851",
"ServerType": "InProc",
"ServerPath": "C:\\Windows\\System32\\oleaut32.dll"
},
{
"Name": "StdPicture",
"CLSID": "0be35204-8f91-11ce-9de3-00aa004bb851",
"ServerType": "InProc",
"ServerPath": "C:\\Windows\\System32\\oleaut32.dll"
}
]
}
]
}
```
## Example Code
```
ForsHops.cpp code left out for brevity
```
The final C/C++ code should include every function and variable declaration needed to compile and run successfully. Don't leave out any functions from the example that are necessary for the code to work.In this example, we’re targeting a specific bug class, so we provide the LLM with a concrete example. Example code significantly improves reliability for discovering variations like this, but it’s not always feasible for more open-ended research scenarios. To generate some of the information, we feed an LLM details about both the COM class and the type of bug we’re after. We utilize various prompt templates with different information depending on the specific use case.
Results
We discovered multiple trapped COM objects capable of lateral movement on Windows 11, including the FileSystemImage class shown above. The IOCs for each implementation overlap significantly with the original ForsHops POC. We uploaded the unedited code from GPT-4.1 to GitHub. Our .NET assembly in the following demo just writes “Hello, world” to C:\test.txt.
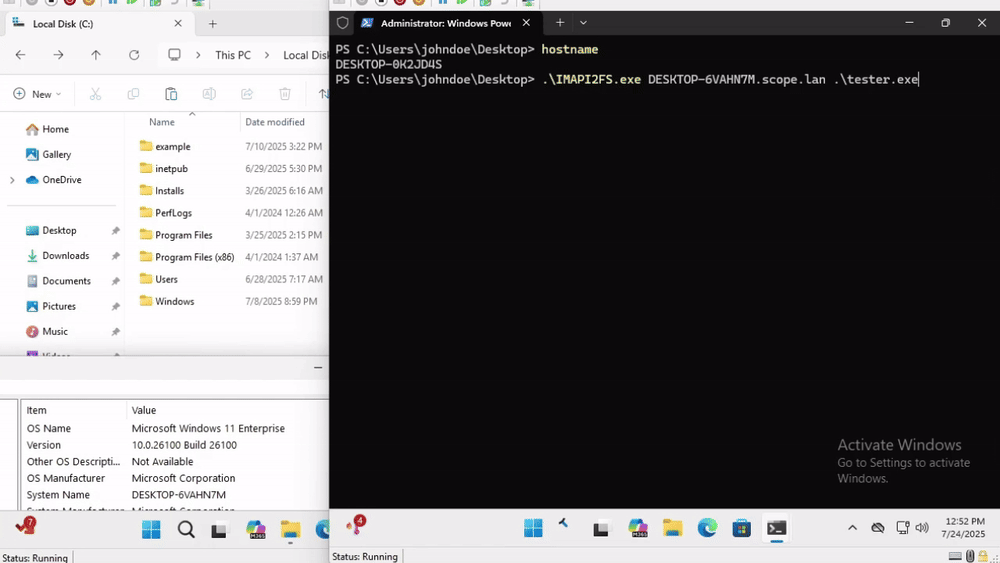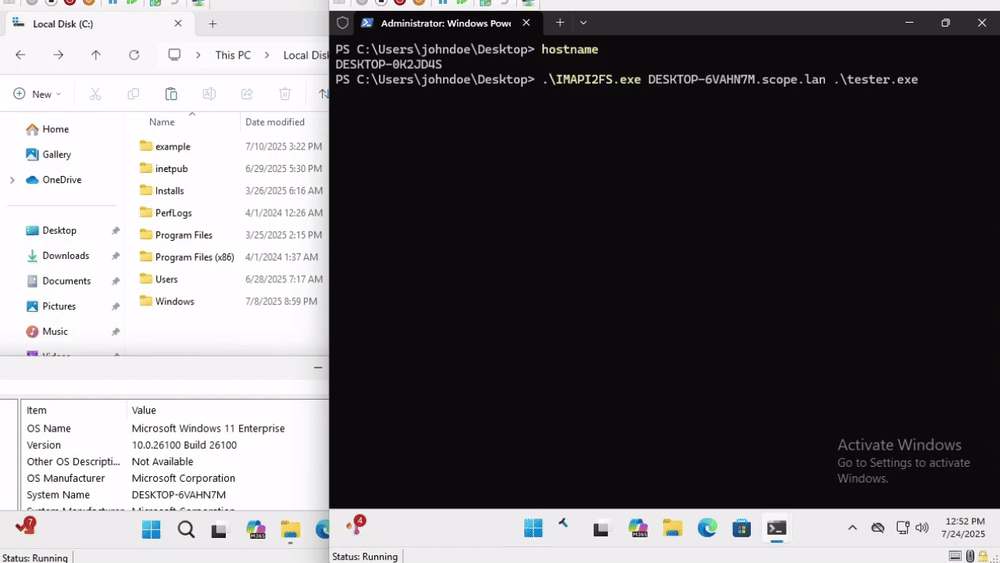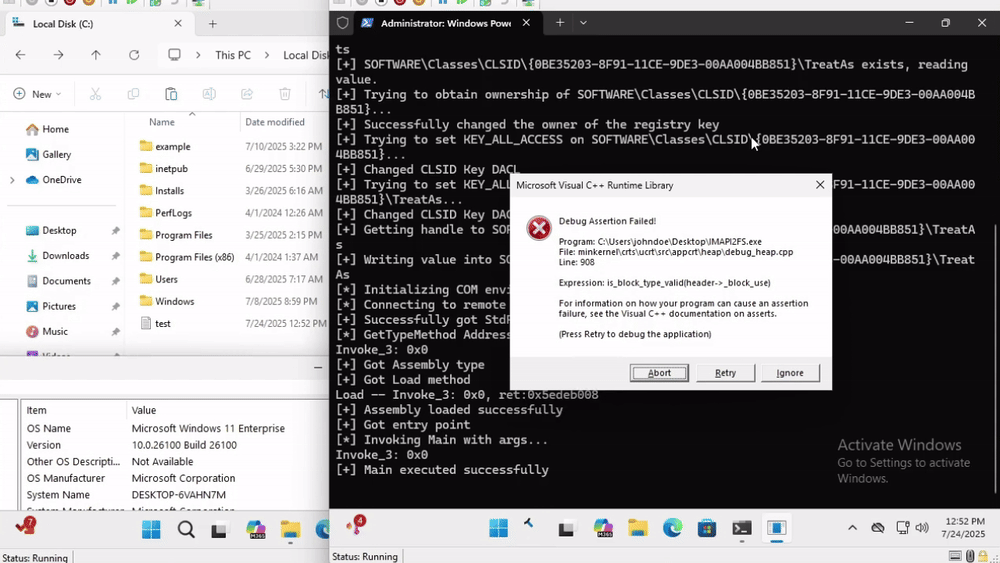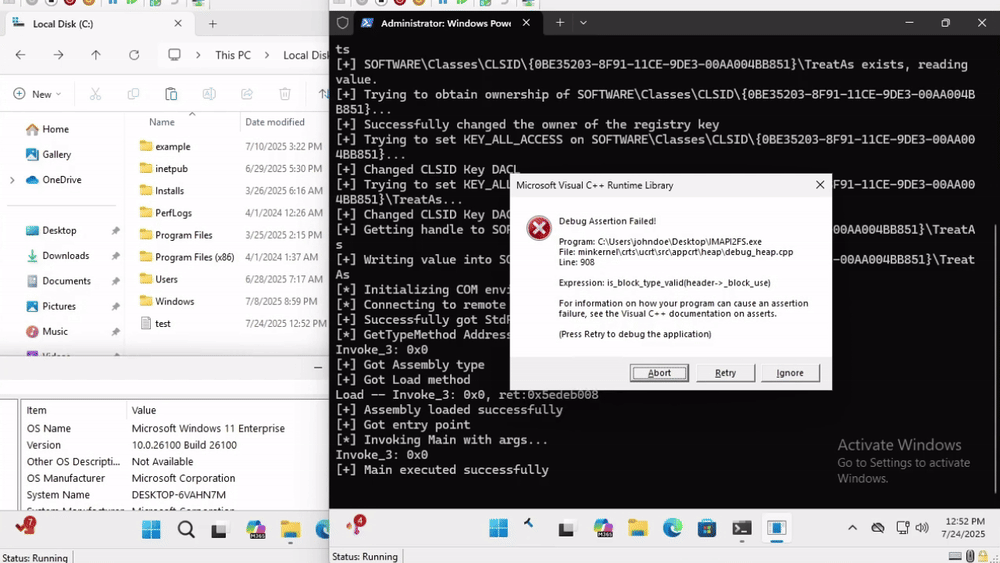
As you can see, the client crashes after successfully executing our .NET assembly on the remote host. We leave the task of creating a production-ready tool as an exercise to the reader.